Market Analysis PET Providers
In 2023, we performed a small-scale market analysis to obtain a picture of the current state of the PET market. In this article we evaluate some of the main insights from this analysis, giving some insight into the current state of the PET market.
Preserving privacy in data sharing is no longer a futuristic vision, it is a reality made possible by the Privacy-Enhancing Technology (PET) market. In short, PETs are a range of technologies that enable multiple parties to gain insights based on their shared data whilst preserving the confidentiality of the data. Our current program ‘Alliance for Privacy Preserving Detection of Financial Crime’ [APP-DFC], a partnership between De Volksbank, TMNL, CWI, ABN AMRO, Rabobank, and TNO, strives for the collaborative detection of financial crime using PETs. We foresee a demand for these technologies for effective and privacy-preserving financial crime detection in the near future, and we think it likely that commercial PET solutions will have an important role to play in realizing this future.
In 2023, we performed a small-scale market analysis to obtain a picture of the current state of the PET market. We have sent out questionnaires and conducted follow-up interviews with eight PET providers of different sizes and located in different countries. Their maturity ranged from new entrants, to pioneers with nearly two decades of PET development under their belt. The majority of these providers have made PETs their core focus. Their offerings enable others to identify their desired applications and setting up the governance for their own PET implementations without requiring a deep understanding of the PETs on a technical level.
In this article we evaluate some of the main insights from this analysis, giving some insight into the current state of the PET market.
Different technologies
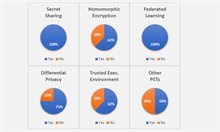
To start with perhaps the most obvious question: which privacy-enhancing technologies do the participating providers offer?
Here, we see a good variety on offer with all of the technologies we inquired about being represented (see Figure 1). Other PETs that were mentioned are synthetic data generation and statistical disclosure control. We note that the same PET may be employed in different ways. In particular, while Secret Sharing is often used to implement multi-party computations, some providers use it primarily for key management.
PET platforms
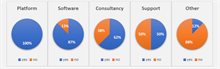
While privacy-enhancing technologies have been offered for some time, we see a relatively new trend emerging in the market – the rise of commercial parties providing PET platforms. In fact, as shown in Figure 2, all of the providers we spoke to offer some form of platform, with ready-to-use solutions for specific problems coming in second, followed by tailored software solutions. These platforms serve as comprehensive infrastructural frameworks, making (general) PET solutions more accessible to end users.
These platforms allow for a one-time setup, instead of requiring a new ad-hoc setup for every separate analysis. Ideally, the platform supports the implementation of multiple PET technologies such that they can complement one another or the one best-suited for the problem can be selected. In our surveys we have seen that a fair number of providers indeed work on multiple PETs or combinations thereof. The use of a PET platform can make PETs much more accessible and as such facilitate their adoption.
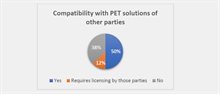
Interoperability
Looking at interoperability, some PET providers offer the possibility to combine services with other complementary PETs, even when provided by another PET provider (see Figure 3). We however found no interoperability between PET platforms on similar functionalities. For example, Secret Sharing or Homomorphic Encryption may be used in conjunction with Federated Learning to enhance privacy of the latter, but collaboration between two parties typically requires them to be using the exact same platform(s). Considering the lack of direct interoperability between platforms utilizing the same PETs, they inherently could carry the risk of a vendor lock-in. It is worth noting that the platforms typically don’t require PET-specific expertise from their users. This means that transferring an algorithm designed in one environment to another is likely to be feasible, if not cumbersome. Note that factors such as open APIs, and accessible support can greatly alleviate the risk of lock-in.
Governance
Consider a group of people at a birthday party that are curious about their average income. They can trivially compute this together in a secure way by using a technique like secret sharing. But what if shortly after, one of the attendees leaves and the others again compute their average income? In that case sensitive data will be compromised because even if the computation itself is again done securely, the people who participated in it will now be able to easily deduce the income of the person who left. So, it is clear that some restrictions should apply. But who gets to make the rules, and when and to whom do they apply?
Proper governance is key, but can be approached in different ways. One can make legal agreements between parties that make the required data available and allows for executing analyses within the pre-agreed upon terms. Logging functionality of the platform may provide audit trail. Another option is to use the PET platform to not only handle data and computations, but also to facilitate the governance by allowing parties to indicate preferences, vote on rules, and automatically enforce those rules (e.g. through statistical disclosure control). If this is done well, it is possible to securely publish[1] data once and make it available for a range of analysis as long as they fit within the terms of the established agreements. Importantly, this unburdens the analysts from legal constraints, making it so that they can focus on getting the results they’re after without concern whether the analysis is allowed.
Deployment and transparency
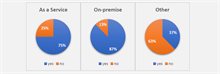
When adopting software developed by another company, different deployment options may be available. We differentiate between “as a service” and “on-premise” services. In the first case the software is hosted by the provider whereas it is run locally in the latter case. As a customer, this is about finding a balance between costs, convenience, performance, and security. We found that at this time most providers are flexible in this regard, either expressly offering both options or willing to adapt to customer demands. In some cases a hybrid approach is utilized (Figure 4).
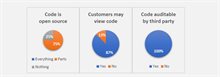
When we look at transparency of the PET solutions, the majority of providers indicate that parts of their source code are open source (Figure 5). This is to be expected as it is a best practice in the cryptography community to have code openly available for public scrutiny. Parts of the code pertaining to other aspects of their solutions is where the PET providers try to differentiate and hence are not unsurprisingly typically not open source. Even so, some providers are taking steps to open source part of their solutions, e.g. to enable interoperability with existing open-source frameworks. And, should there be a need from the customer, all providers indicate that it is possible to have the code audited by a third party and most appeared willing to let the customer view the underlying code themselves.
Relevance for the financial sector
With the availability of these commercial solutions, one might wonder what work is left to be done. Both for general applications, but also for the financial sector in particular. Do we need further innovation, and if so, what is it that is left to explore?
Mainly it comes down to there not being a one-size-fits-all or best practice that turns an arbitrary analysis into a secure and efficient implementation. While many problems can easily be boiled down a limited set of basic operations for which sufficiently efficient solutions are available, some more complex problems require a tailor made approach. For example, relatively little work has been done on network analyses, a domain that is crucial for AML and similar efforts. We note that it appears that this can be attributed to lack of customer demand more so than inherent limitations of the platforms. This is certainly not to say there is a lack of know-how, but the fact remains that there are few off-the-shelf solutions and there is quite a bit left to explore.
Another observation is that providers have so far mostly focused on what is known as ‘passive security’ because it suffices for the use cases they typically work on (i.e. mostly-trusted parties collaborating within the same country). ‘Active security’ yields stronger guarantees that they do not currently need at the expense of requiring more computing power. However, it is generally acknowledged that active security could be warranted in cross-border collaborations potentially involving parties that are trusted to a lesser extent. Again a scenario that is not unlikely in the world of international finance. Transitioning from passive to active security is typically not as simple as flipping a switch, which is why this topic has been actively worked on in the Alliance project.
Towards the future
The market for PETs has been maturing rapidly, with viable solutions to many a problem becoming more and more accessible. Beside the rapidly expanding collection of PET algorithms we observe a trend towards utilizing PET platforms rather than individual ad-hoc solutions. We expect that such platforms will make these technologies more accessible, supporting our vision of a future where the use of PETs is commonplace. Another important development in this regard concerns the integration of governance. Implementing technology alone is not enough.
We know that for many applications, the collaborative nature and differences in standards of different markets still warrant tailor-made solutions. These can later on be adopted by PET service providers, alike in the case of TNO’s Alliance project. But whenever you are faced with a challenge involving sensitive data it is good to keep these ready-to-use commercial offerings in mind.
Acknowledgements
We would like to thank our contacts at Tune Insight, IBM, Inpher, Roseman Labs, BranchKey, Duality, Linksight and the other respondees for their participation in the market analysis.